SSH? What it is
SSH also Known as Secure Shell, a secured network protocol used for remote login from one system to another system over a network. Additionally, it provides a cryptographically secured connection for strong authentication. It is a strong alternative to non-encryption based protocols Like Telnet used for remote login and FTP, a file transfer method. Except for Microsoft, SSH is used in most of the operating systems.
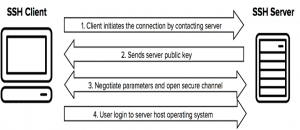
Working of SSH
SSH works on Client-server model, where Client request for data from the Server. SSH by default operates on standard TCP port 22.
Let’s understand it with the help of diagram
The most common authentication options using SSH are Password and Public Key authentication. Firstly we will cover authentication using Username and Password on Linux operating system.
Also Read: 10 Best Linux Apps for Users – 2018 Edition
Password Authentication in SSH
Make sure to have two Linux network and firewall is turned off, for that follow these simple steps:
For enabling Firewall temporarily use ‘iptables -F‘, but for permanent Let me tell you a trick, follow these
- Change directory using ‘cd /etc/profile.d/’.
- Create file custom.sh using ‘cat >custom.sh‘ or by any other command that you know, enter ‘iptables -F‘ in this file.
- Save this file and return to home directory by ‘cd‘
- Reboot your system.
- You are done on after bootup you can check your iptables configuration using ‘iptables-L‘.
For enabling SELinux, kind of firewall follow these step
- Firstly check status using ‘Sestatus‘.
- if Enable type ‘vi /etc/selinux/config‘, this will open config file for SELinux edit ‘enable’ to ‘disabled’ where SELINUX is written.
- reboot your system
To set the IP address:
- Use ‘system-config-network’ command to open IP configuration window
- Navigate to eth0 or eth1 whichever is available
- Remove dot from DHCP using the spacebar
- Give static IP, and set On Boot using the spacebar
- Save your changes.
- Type ‘vi /etc/resolve.conf‘ replace four doted number with IP address that you gave to your system.
- Save the file
- Enter ‘service network restart’.
- Reboot your system and you are done.
For SSH, make sure that systems ping each other.
- To check type ‘Ping IP_of_other_system‘.
- If pinging type ‘ssh username@ipaddress‘ for remote login to another system.
- After this, you will be asked for the password of the system.
- If you enter correct password you are ready to use the system remotely.
Advantages of Password type Authentication
- Simple to use
- Simple to deploy—since the operating system provides the user accounts and password, almost no extra configuration is needed.
Disadvantages of Password type Authentication
- Security is entirely based on confidentiality and the strength of the password.
- Does not provide strong identity check.
To overcome these problems we have Public Key Authentication technique.
To set up public-key authentication using SSH on a Linux:
- Type cd .ssh/id_rsa
- Generate Key using ‘ssh -keygen‘, this will generate two keys one public and one private key, further save the generated key in ‘./ssh/id_rsa‘.
- You can also give ‘passphrase for two-phase authentication, which acts as a security question when you login remotely.
- To view both keys you can type ‘cd .ssh/‘ and then use ‘ls‘ command.
Once we have generated keys we have to pass public key to the client or another user.
- Make a directory for other user using ‘mkdir .ssh‘, same name as in user1.
- Give permission using ‘chmod 700 .ssh‘ here 700 means the only owner of the file can read, write and execute that file.
- In user1 enter ‘cd .ssh‘ to navigate to .ssh directory.
- Copy the key file from user1 to user2 using ‘SCP id_rsa.pub user2@Ipaddress:/home/user2/.ssh‘.
- Now in user2 enter ‘ls .ssh/ ‘, you will notice id_rsa.pub added to the list of files.
- Type ‘cat id_rsa.pub >>authorized_keys‘, to concatenate content of id_rsa.pub to new file authorized_keys, this it saves the keys as a backup.
- Afterwards try to use ssh in user1 to access user2,e.g ‘user2@Ipaddress‘.
- Now there will be no need for a password, but yes if you have set a passphrase you have to enter it here.
Applications of SSH
- Secure Shell (SSH) is a cryptographic network protocol for operating network services securely over an unsecured network.
- SSH provides a secure channel over an unsecured network in a client-server architecture, connecting an SSH client application with an SSH server. Common applications include remote command-line login and remote command execution, but any network service can be secured with SSH
- SSH uses public-key cryptography to authenticate the remote computer and allow it to authenticate the user, if necessary. There are several ways to use SSH; one is to use automatically generated public-private key pairs to simply encrypt a network connection and then use password authentication to log on.
- Another is to use a manually generated public-private key pair to perform the authentication, allowing users or programs to log in without having to specify a password. In this scenario, anyone can produce a matching pair of different keys (public and private).
- The public key is placed on all computers that must allow access to the owner of the matching private key (the owner keeps the private key secret). While authentication is based on the private key, the key itself is never transferred through the network during authentication. Secured Shell only verifies whether the same person offering the public key also owns the matching private key
- SSH is typically used to log in to a remote machine and execute commands, but it also supports tunnelling, forwarding TCP ports and X11 connections, it can transfer files using the associated SSH file transfer (SFTP) or secure copy (SCP) protocols. SSH uses the client-server model.
Difference Between SSL and SSH
The other thing to Know is SSL (Secure socket layer), let us simply see the difference between SSH and SSL
| SSL | SSH | |
| Abbreviation | Secure Socket Layer | Secure shell |
| Port | 443 | 22 |
| Application | For Encrypting Communication between Browser and Sever | For Encrypting Communication between two computers |
| Adopted by | E-commerce, Banking, Social media, Government | Widely used by the networking industry |
| Authentication | via Public/Private key pair |
|
Conclusion
In this article we have shown you how SSH is used to transfer data in both Password and Public key authentication, you will be glad to know that tech giant Amazon also uses Public key authentication in AWS and its other services. We also briefly discussed differences between SSL and SSH.
Also Read: 10 Best Linux Distros — Ultimate Distro Guide 2018