What and Why Tor Browser?
For those concerned about the security of their data in the network or those who like to surf anonymously for marketing issues, TOR browser is there for you which focuses on these details that many users demand from current browsers.
Tor is an abbreviation of “The Onion Router” (literally, the Onion Router) is an independent and cross-platform web browser, is based on Firefox and has been updated in its seventh version, more stable and with more improvements in the aspects of security and user privacy.
Tor is based on an objective, which is the creation of a communications network in which the identity and data of the users are protected, which does not reveal its identity, that is, its IP address and, in addition, maintains the integrity and secret of the information that travels through it.
Tor recently released a new security level. The new changes include encryption algorithms, enhanced authentication, and a restructured directory system. In addition, the new “onion” domains will be longer so that the “onion” addresses are entirely private.
How Tor Works?
Now that you know what Tor is, let’s see how it works and how to use it.
The use of Tor is relatively simple. Just download and install the Tor browser, which will replace Chrome, Firefox or your usual browser. All your activities on the Tor browser will be confidential and secure.
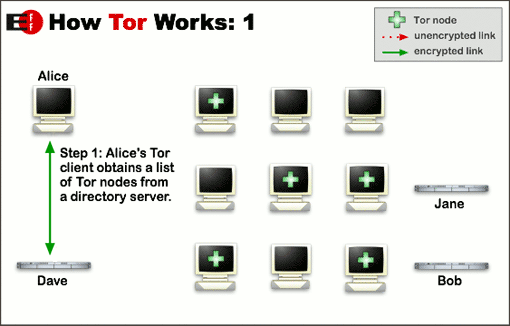
Tor groups your data into encrypted packets before they enter the network. Tor then removes the portion of the package containing information such as source, size, destination, and timing, all of which may be used to obtain more information about the sender (ie you.)
It then encrypts the rest of the grouped information before finally sending the encrypted data through many different servers, or relays, randomly, to avoid being tracked.
Each relay decrypts and then re-encrypts the minimum amount of data required to know where they come from, but is unable to track the information beyond that minimum.
The many encryption layers used by Tor to ensure anonymity are similar to those of an onion, hence the name. The illustration below is an excellent explanation of how Tor works.
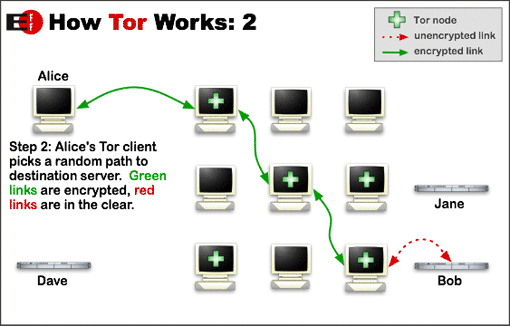
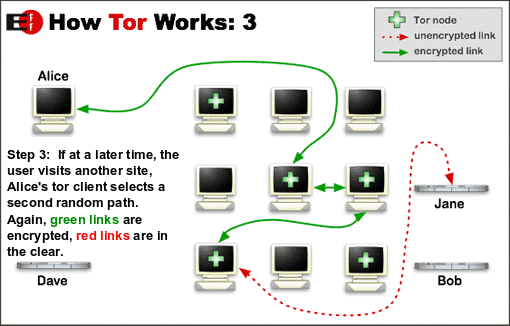
Why not use Tor?
The main disadvantage of Tor is its performance, or rather his lack of performance.
Since data goes through many relays, Tor is very slow, especially in terms of audio and video. Streaming or downloading can be a nightmare, and this is one of the main reasons why using a VPN or browser with integrated VPN makes more sense for most users.
It’s also important to note that using Tor does not make you 100% invulnerable.
In fact, many people think that Tor can be easily hacked because the exit nodes (the last relay before your information reaches their destination) can view your traffic if the site you are accessing does not use SSL. Using HTTPS instead of a simple HTTP can add an extra level of protection, but it’s not foolproof.
Finally, government agencies can see if you are using Tor. Therefore, although they can not see your activities, they can interpret it as a red flag.
Using Tor with a VPN
Tor can be used with a VPN, although their relationship is relatively complex. You can opt for “Tor-through-VPN” (Tor through VPN) or “VPN-through-Tor” (VPN through Tor), and the difference between the two is considerable.
We will not go into technical details, but it is important to understand the advantages and disadvantages of each option. In addition, be aware that whatever configuration you use, your performance will be significantly reduced.
Tor and VPNs slow the speed of the Internet, and the combination of the two makes this drop even more noticeable.
Also Read: Top 10 Free and Paid VPN Apps for Android Devices
Tor-through-VPN (Tor through the VPN)
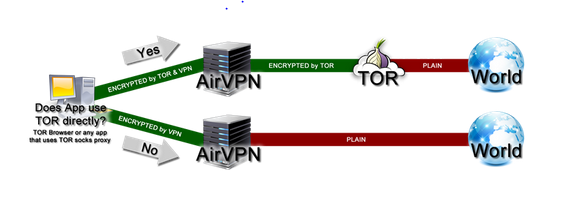
With the “Tor-through-VPN” option, the relationship is:
your computer -> VPN -> Tor -> Internet
The advantage of this is that your ISP (Internet Service Provider) will not know that you use Tor, even if he can still know that you use a VPN. In addition, the Tor entry node will not see your IP address, which is an excellent additional level of security.
The disadvantage of this configuration is that your VPN knows your real IP address, and you have no protection against malicious Tor exit nodes.
Some VPN providers (such as NordVPN, Privatoria and TorVPN) offer Tor-through-VPN configurations. It’s a good option, but it’s not nearly as secure as using the Tor browser, where Tor encryption is done end-to-end.
VPN-through-Tor (VPN through Tor)
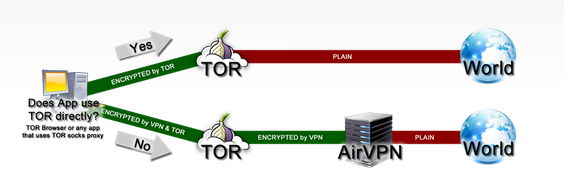
With the “VPN-through-Tor” option, the relationship is:
Your computer -> Tor -> VPN -> Internet.
“VPN-through-Tor” is much more secure, ensuring almost perfect anonymity. That said, you need to configure your VPN to work with TOR, and only two services (to our knowledge) allow you to do so: AirVPN and BolehVPN.
Of course, if the restriction on the VPN to use is no problem, “VPN-through-Tor” is a better choice.
First, the VPN provider has no way of knowing your real IP address but sees the IP address of the Tor exit node. If you go that far, we recommend paying with Bitcoin via the Tor browser via the Tor browser, which means that the VPN provider really has no way of identifying you, even if it keeps the logs.
The other benefit is protection against malicious Tor exit nodes since your data is encrypted by the VPN.
This also has the effect of bypassing all the blocks on Tor output nodes (such as censoring), which the Tor-through-VPN configuration is unable to do.
That said, if you do not want to bother with “VPN-through-Tor”, you can still run “Tor-through-VPN” by simply opening the Tor browser after establishing your VPN connection.
Ready For TOR, Let’s Install it
For Ubuntu:
Given the brief explanation of the Tor project, we proceed to explain the installation of this browser in our system.
First, we will have to open the terminal and execute the following commands, which depending on what type of architecture they handle, will be the one indicated for the installation:
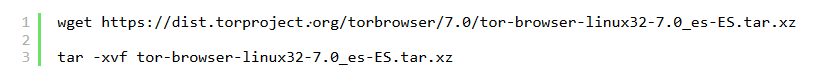
For 32-bit systems:
First, we will have to download the installation package that Tor directly offers and decompress the file when the download is finished.
Then we place ourselves inside the folder that we unzip and run the browser.
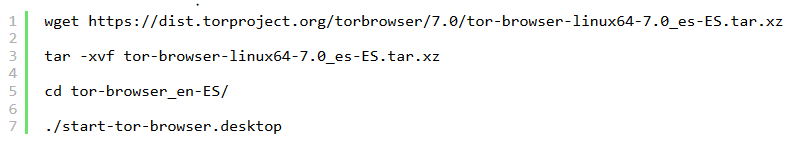
For 64-bit systems.
For systems with 64-bit architecture applies the same process, only that we download the package indicated for this architecture.
When executing this command, the browser’s graphical environment will be opened, as well as the start of our browser which shows us since we have changed our Public IP for another one.
In case of wanting to change our supposed Public IP address, we will have to click on the “Use a new identity” button and that’s it!
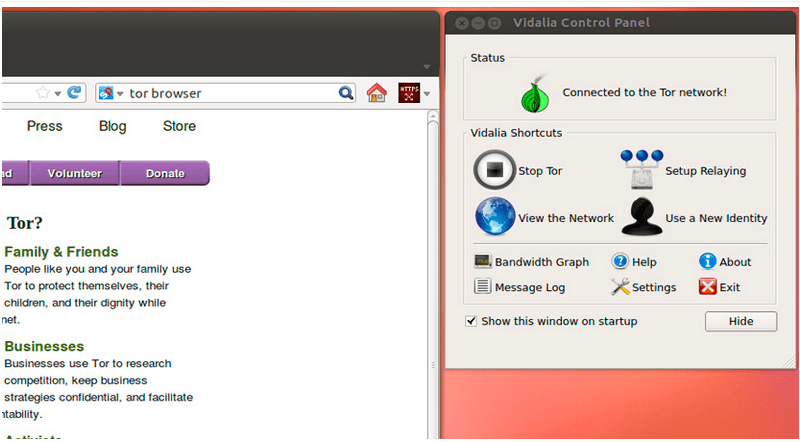
And to stop the service, press “Stop Tor”. Now, we can create a direct access to the system and thus we avoid being in need of the terminal to open Tor.
if you are not comfortable with commands don’t worry just visit the official website here For Windows/Mac/Linux
Windows:
Now Click on connect and you are ready to surf.
Once on the Internet, here are some tips for even more security:
- Access only HTTPS sites, not HTTP. Although Tor encrypts the entire Tor network, Tor does not encrypt traffic outside it, which makes you vulnerable once your traffic reaches the output nodes, since your data is no longer encrypted. This is why you should always use end-to-end encryption such as SSL or TLS, as well as sites using HTTPS. To ensure that you only use HTTPS sites, consider using the HTTPS Everywhere plugin.
- Do not use P2P traffic in Tor. Do not use P2P traffic in Tor. Tor browser does not support peer-to-peer traffic, and will likely be blocked by many output nodes. P2P over Tor traffic threatens your anonymity online because BitTorrent clients send your IP address to BitTorrent trackers and other peers.
- Always delete cookies. You can use an extension like Self-Destructing Cookies to automatically delete cookies.
- Do not use your real e-mail. This sounds obvious, but consider it a reminder. As a certain website explains, indicating your real email using Tor is “going to a costume party with a badge indicating your identity“.
- Do not use Google. Google is infamous for gathering information about browsing habits and searching data from its users in order to increase its advertising revenue. Use search engines like DuckDuckGo instead.
Privacy is increasingly difficult to maintain as the government, hackers and even our beloved Google find more and more advanced ways to hack and control us. Despite its known flaws and vulnerabilities, the Tor Browser is an effective step towards greater anonymity online. However, this is only one piece of the puzzle.
Also Read: What is Secure Shell ( SSH ) And How it is Different From SSL