A Facebook security report has revealed that Facebook user data could be retrieved using JavaScript trackers. The report reveals user data can be tracked by planting trackers in websites that let users log in through Facebook. The data that can be retrieved is not limited to just name and email. But the exploit can be used to catch age range, gender, locale and profile photo. All of this though depends on the access allowed by the user to the website. Once the user logs in using their Facebook credentials, their data can be retrieved by any third party JavaScript.
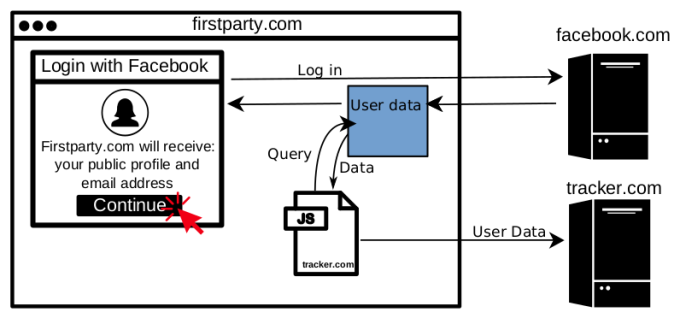
The report:
The report has been given by Princeton’s Center for Information Technology Policy. It lists around 431 of the top one million sites that have some irregular scripts inside their code. The list also included MongoDB which provides cloud database services. After TechCrunch brought the issue to their attention, the website has shut down the script. MongoDB said “We were unaware that a third-party technology was using a tracking script that collects parts of Facebook user data. We have identified the source of the script and shut it down.”
Scraping Facebook for user data is a direct violation of the company’s policies. Speaking to Engadget a Facebook Spokesperson said
“While we are investigating this issue, we have taken immediate action by suspending the ability to link unique user IDs for specific applications to individual Facebook profile pages, and are working to institute additional authentication and rate limiting for Facebook Login profile picture requests“.
The conclusion of the report says that the exposed user data is “due to the lack of security boundaries between the first-party and third-party scripts in today’s web“. Facebook has already been facing a lot of problems right now and it certainly isn’t the best time to discover new loopholes. Facebook could have identified these tracker scripts if it would have done sufficient API auditing.





